What is FlowShield?
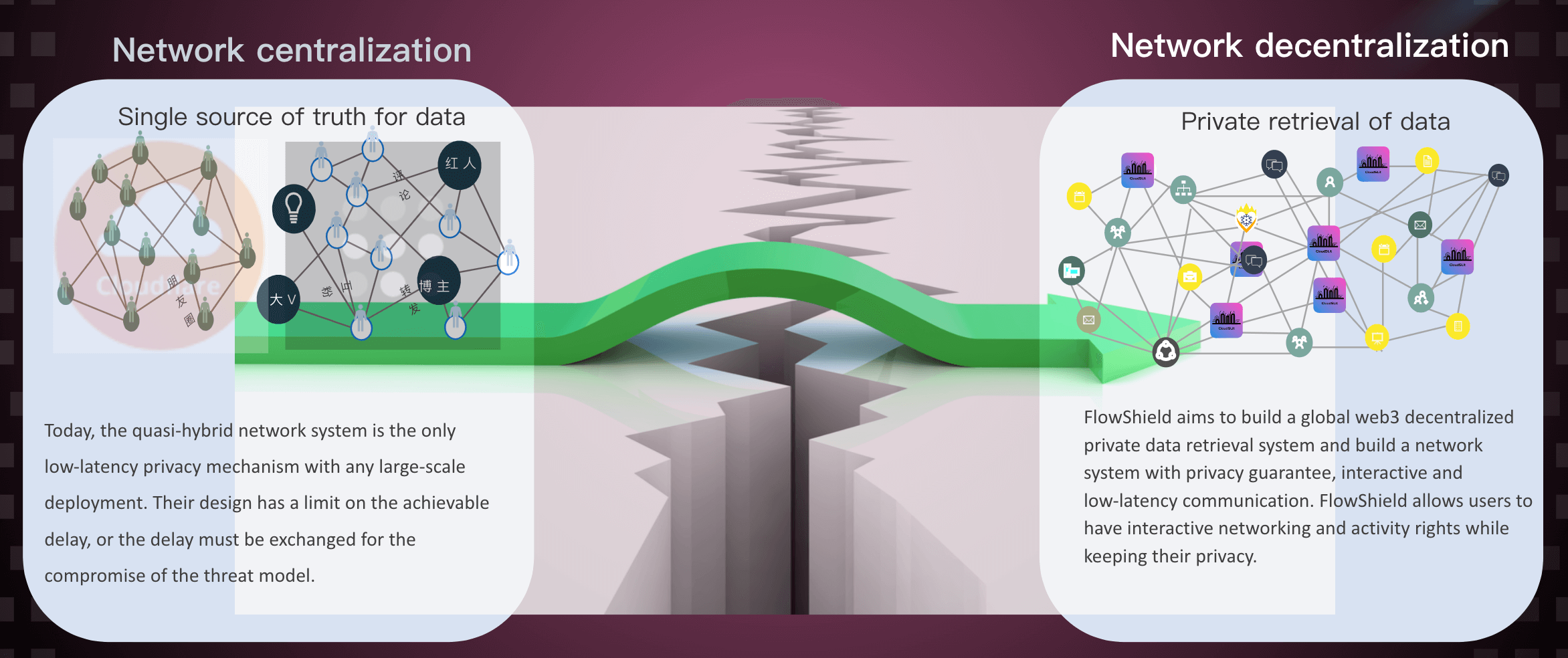
FlowShield aims to build a global web3 decentralized private data retrieval system, and build a network system with privacy assurance, interactive and low delay communication, FlowShield allows users to have interactive networking and activity permissions while keeping their privacy. FlowShield credentials encrypt and embed data required by specific services (including zero knowledge proof of private data). The authentication method of these credentials is decentralized and public, and will not disclose any links between users and the services they want to access. FlowShield helps users regain the privacy and security information eroded by the giants under web2, making the current global hot zero trust network technology combined with web3 better help users master Their own security and privacy data, and provide users with good zero trust security network products and platform experience.
Motivation
At present, there are very limited systems that can be used for privacy guaranteed, interactive and low delay communication, and it is very difficult to build systems with these three characteristics. The solutions developed so far focus on the traditional Web model of a single trusted source data publisher (as opposed to content addressing systems that can replicate data in advance), And there are defects in the delay and threat model it incurs.
For the Protocol Labs RFP-014 file, we propose our unique solution and develop a deployable prototype.
Present Situation
The most widely deployed reader privacy approach relies on hybrid networks and multi hop systems similar to hybrid networks (Nym, Tor) or trusted hardware (SGX).
Each of these solutions requires trade-offs. Tor and Nym will incur higher delay costs. The additional network hops used by these systems make it difficult for them to compete with web2 CDN in speed. Today’s multi hop systems have not considered how to optimize the performance of non Web cases with self certified, cacheable content.
Hardware solutions such as SGX have been used as privacy solutions in many scenarios, especially Signal. This abstraction provides low latency, but relies on trust in centralized server operators and hardware manufacturers.
Other potential improvements to the balance of security and privacy have been developed in the academic literature, but have not yet crossed the innovation gap into production. These include cryptographic systems such as FHE, the core of DARPA’s DPRIVE program, And a large-scale scalable anonymous communication system like PIR Tor. From blind token to zero knowledge proof and statistical data structure Promising technologies may also play a role in practical systems.

Characteristic
Privacy
FlowShield is a network based on zero knowledge proof and didmechanism, which provides a strong guarantee
to prevent the leakage and harvest of network layer metadata.
It is a universal privacy overlay network, which is agnostic and can connect almost any other digital application or service,
Enable individuals and digital service providers to ensure their own or users’ privacy.

Low Latency
The quasi hybrid network is used to stimulate competition. Users choose the nodes to use, and the initiative will be
attributed to customers to achieve a decentralized single hop system,
It guarantees both privacy and low latency.

Interactive
FlowShield node operators are rewarded based on stability proof to ensure everyone’s privacy.
FlowShield only uses data packages that can meet the requirements of service stability certification, and minimizes unnecessary environmental costs.
There is a competitive relationship between node operators. Users can freely choose the nodes to use, providing convenient interaction.

Network Quality
Network quality verifier can ensure that network providers provide a good network service environment and support the benign development of services.

Component Design
Anyone can run a complete node, which carries the metadata of the decentralized network and provides a metadata networking and transaction matching platform.
For all users’ and Dao’s data, we use Filecoin’s web 3.storage to store user data separately.

Our node can realize automatic networking through peer discovery and routing through libp2p kademlia DHT and IPFS networks, The Pub Sub function of libp 2p enables data synchronization between multiple nodes.
We use smart contracts. Provide a secure transaction process and a secure transaction environment.
Client software users connect to the provider to establish a zero trust network security tunnel.